Do you know what Uber has of you and how can you review and protect you?|The financial
Cuando usted utiliza Uber o Uber Eats se generan datos del servicio solicitado. ¿Cuáles son esos datos? ¿Quién los puede ver?
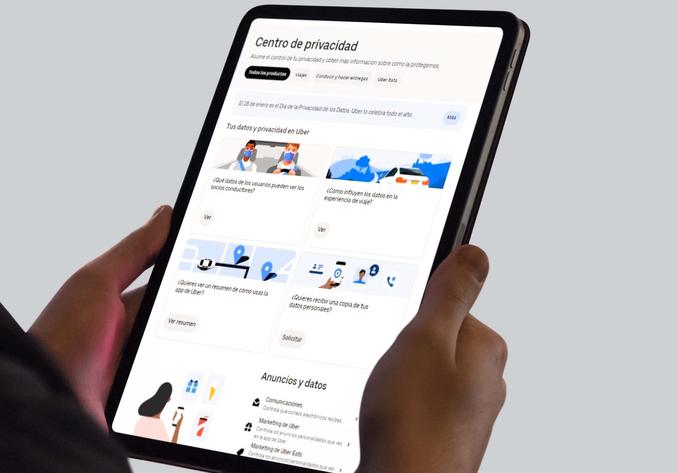
Both customers and for collaborating or delivery partners know what the stored personal information is, the firm has a privacy center that each one enters with the information of their own account.There you can also review the company's policy or approach on this matter.
Thus you can review what information the collaborating partner sees on a trip, for example, since he requests it until after being completed.For example, partners do not have access to the user phone number and vice versa;Nor of the parties knows the qualification that everyone grants on each trip.
In that center you can see your data and others of interest as a summary, download a copy with the information that is collected when using the application and configure the emails you receive or the ads.
You must remember that data security and protection is a shared responsibility.
Uber explains that it uses security methods such as authentication, encryption, fraud detection and software development to protect personal data and promote safety in the use of its platform
It is up to you: do not share your access passwords;If a communication is received from Uber, you must verify the email sender making sure it is @uber.as their official channels.
You must also remember that Uber does not send redirection links and does not request confirmation of information outside the application or the official website.
The company reiterates that the support equipment has access to the data it needs to serve and will never request passwords or codes.The user must distrust, therefore, from the messages that offer money or urgent content (such as “their account will be deactivated if it does not confirm their data”).
The user should not share or disseminate the four -digit verification code received by short text message or SMS to their cellular number.This number is for exclusive use and no Uber support agent will request it.
Another reminder is that Uber does not offer services that are not present in the application."The only way to request a service is through its applications, you should not fall into deception with services offered by other ways, such as social networks," the company reiterated.
The above recommendations - realized within the framework of the International Day for the Protection of Person, use services or buy products.Companies must also implement transparency mechanisms and comply with the regulations.
"A company committed to the protection of personal data provides added value, since it generates confidence to its customers, and allows it even more easily entering international markets that could have higher demands regarding the management of people's data,"said Gabriela Alfaro, data protection specialist at Nassar lawyers.
All these measures are not secondary.
Check Point Software Technologies, a digital safety solution supplier, reported that cyber attacks increased 50% in 2021 globally.In the last quarter of last year, the firm detected 925 weekly cyberattacks on average by company.In Latin America the average was greater (1.118 weekly attacks).
Imperva Research Labs warned that cyber attacks affect the sensitive information of companies and also personal data: 74% of stolen data are personal, 15% consisted of the theft of credentials (passwords) and more than 10% of the informationcredit cards.
Errores exponen a empresas y usuarios
Companies must have a legal basis for the processing of personal data and comply with the main provisions of the person's protection law against the processing of their personal data (no.8968).
The main and most common legal basis is the informed consent, which must meet the requirements established in that law.You must also establish internal policies and manuals on the correct handling of the personal data of your customers, suppliers and personnel, and issuing an action protocol that must include a staff training, updating and awareness manual, among others, among others.
Another obligation is to establish the procedures to answer doubts of the data holders and implement adequate security measures that allow to ensure the integrity of the information.
Although the law already has more than 10 years of having entered into force, there are many companies that do not know the obligations and responsibilities in the management of personal information.
Nassar Lawyers indicates that many companies register and treat personal data without the reported consent of the holder or, when they have a consent, they use the data for a different purpose from which the head.
Another error is misuse by data staff, ignorance of applicable sector standards (for example, in electronic commerce) and companies do not usually corroborate if they are complying with legal provisions.
The risk is double: legal sanctions, which according to the severity of the offense range up to 30 base salaries or the suspension of the database for up to six months.In addition, when a misuse of information is revealed, the company or institution is affected its reputation or image, causing customers not to make more transactions with the company.
The lack of data protection facilitates the attacks, extortion and fraud of cybercriminals.
"Each person, company or home must seek forms and tools to protect their social and material assets from cyber criminals, since most attacks come from inside the facilities or homes due to the poor management of technology,"Pedro Álvarez, Grupo Cesa Cloud Technology Manager warned.
Both companies and a users must follow good practices for the protection of their information."Any business or personal data is a potential objective for digital criminals," said Joey Milgram, general manager of safe solutions in Costa Rica.
Recuerde
Grupo CESA and Safe Solutions recommend users to protect their data:
—Cuide sus redes sociales: no incluya números telefónicos, información bancaria o su ubicación.
—Cambie sus claves: estar constantemente alternando las claves que maneja le ayudará a tener una circulación constante de la misma y así evitar que puedan hackearle su cuenta en cualquier momento; también verifique que las contraseñas sean difíciles de descifrar.
—Evite ingresar a páginas gratuitas para ver películas: estas páginas podrían solicitarle información delicada que podrían utilizar los criminales para atacarle.
—Asegúrese que tiene aplicaciones de seguridad en sus dispositivos: ya sea firewall o antivirus.
—Mantenga sus espacios seguros lo más privado posible: exponer su lugar de trabajo o estudio le dará información a posibles atacantes de dónde pueden extraer su información, cuide su privacidad.
—Intente no conectarse a redes públicas: Esto podría causar que la brecha de seguridad que intenta mantener a diario se caiga al exponer su información a una red pública.
—No guarde archivos con claves en sus dispositivos: si alguien roba alguno de estos productos podría ingresar saquear lo que tenga bajo esas claves.
—No entregue información confidencial por Internet ni por teléfono: sus entidades bancarias y públicas harán saber por medio de sitios oficiales qué información solicitan en llamadas y páginas y qué no.
—Use contraseñas fuertes: utilice claves alfanuméricas y de doble autenticación.
—No brinde demasiada información personal en sus publicaciones en redes sociales.
—Revise la configuración de privacidad y realice los ajustes necesarios para evitar que su información como publicaciones, ubicaciones y otros detalles sean accesibles.
—Lea las políticas de privacidad: al aceptar términos y condiciones en apps o sitios web está otorgando acceso a contenido (fotos, mensajes, ubicaciones y fechas, entre otros datos personales) y se expone a que las aplicaciones compartan o vendan datos a terceros.
—Evite ingresar a links desconocidos o abrir correos de dudosa procedencia: los enlaces y correos maliciosos es una de las tácticas más utilizadas por los ciberdelincuentes.
—Evite utilizar redes públicas: al conectarnos a redes wifi públicas, las operaciones quedan expuestas, vulnerando los datos, tráfico e identidad ante los delincuentes cibernéticos.
—Evite realizar transacciones bancarias o consultar datos sensibles en redes wifi públicas (en cafeterías, restaurantes, aeropuertos o parques) si por alguna razón debe utilizarlas, y asegúrese de cerrar todas las sesiones una vez que haya finalizado el trabajo y desactivar su dispositivo de la red pública.
